What is DMARC?

Explore the essentials of DMARC. Learn how DMARC can protect from domain from phishing and spoofing attacks
What if your best customers received a spam email with your company’s name on it?
Sounds unsettling, right? After all, among the repercussions are a damaged brand image and compromised security.
Unfortunately, this scenario is quite common, and it’s a result of email spoofing — when scammers send emails while pretending to be someone else.
Spoofed emails use a legit-looking email address in the “From:” field, but the email doesn’t actually originate from the company’s servers.
Domain-Based Message Authentication, Reporting, and Conformance (DMARC) is a security protocol that protects the sender reputation by giving you control over spoofed emails that use your domain.
Here’s a closer look at DMARC and how it can prevent your organization from being impersonated.
How does DMARC fit into email authentication and security?
When you send a company email from your app, the “From:” address is automatically set and locked to your account address. But technically savvy scammers have ways to connect directly to email servers and modify the “From:” field before a message is sent.
DMARC is an email protocol that allows you, as a domain owner, to set a policy regarding emails that only pretend to be sent from your domain. DMARC is the final security checkpoint after the Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM). Together, these email protocols create a triple layer of protection against spoofing and phishing.
How does DMARC work?
DMARC itself doesn’t conduct any new email verification. It just tells your email provider how to act based on the results of the SPF and DKIM, which both check the authenticity of a message.
Role of SPF and DKIM
SPF is the first security check to ensure an email comes from an approved mail server for your domain. If the email doesn’t originate from one of the legitimate sources in the SPF record, it fails the SPF check.
DKIM then analyzes whether the email content itself has been tampered with. It looks for a special encrypted code in the email header that acts like a digital signature. This signature proves the email wasn’t modified during delivery. If the email’s signature doesn’t match the domain’s public encryption key, the DKIM check fails.
If the email passes both SPF and DKIM, it will be considered real and delivered to the inbox. But if it fails either SPF or DKIM, the email provider follows the rules in the DMARC policy for handling it.
Action based on DMARC policy
Your DMARC policy states what your email provider should do with emails that fail SPF or DKIM. You can choose to monitor the email, block the fake email completely so it never gets delivered, or send it to the spam folder.
DMARC compared to SPF and DKIM
Here’s a comparison of DMARC, SPF, and DKIM, as well as the role each protocol plays.
| SPF | DKIM | DMARC | |
| Purpose | Validates the sender’s IP address | Validates the email’s content and connection with the sender’s domain | Tells what to do with emails that fail SPF and DKIM |
| How it works | SPF checks if emails come from an authorized server by comparing the sender’s IP against authorized IPs | DKIM uses cryptographic signatures to sign email parts. Receiving servers use the public DKIM key to verify emails weren’t altered | DMARC allows domain owners to set policies on how to handle emails that fail DKIM and SPF |
| Strengths | Prevents unauthorized servers from sending emails on behalf of your domain | Confirms that emails weren’t tampered with and that they come from an authorized domain | Prevents spoofing by requiring alignment between SPF and DKIM |
| Limitations | SPF only checks the return-path address, and can be bypassed by attackers who spoof the “From” address | DKIM doesn’t validate the “From” address or subject line by default | DMARC requires SPF and DKIM to be properly set up, and a strict policy can block good emails |
Why is DMARC important?
At this point, you might be wondering — Isn’t this what spam filters are for? While basic spam filters do catch junk mail, they rely on basic spam signs like suspicious wording or links.
Let’s look at some of the main DMARC benefits that make it an essential email security layer above a simple spam filter.
Higher email open rates
When SPF, DKIM, and DMARC aren’t set up correctly, your real emails could automatically get blocked, marked as spam, or delivered with warning messages by email providers.
If your email performance metrics start dropping unexpectedly, you should confirm that these protocols are in place.
When one of our clients had unexpectedly low open rates, this was the first thing we checked.
As it turned out, their email protocols weren’t configured correctly, which was why their open rates were 15% and dropping. After setting up SPF, DKIM, and DMARC with a fresh domain, their first-touch open rate rocketed to 80%.
Spotless brand reputation
Scammers are getting better at making phishing emails look real and convincing. Generative AI can generate hundreds or thousands of personalized phishing messages, leading to a massive 1,265% increase in phishing emails since ChatGPT was launched in November 2022.
With the right DMARC setup, you can ensure your customers won’t see an advanced AI-generated phishing attempt with your company’s name on it.
An aid for PCI DSS compliance
There are strict data rules for industries like healthcare, finance, and others that deal with private information.
While DMARC isn’t mandatory yet, PCI DSS recommends it as a good practice to keep your emails secure and protect sensitive data—which is actually a requirement from PCI DSS.
Overall cost savings
Think about how much it could cost if you do nothing — the costs of responding to incidents, fines from regulators, compensating customers, and more. The average global cost of a data breach in 2023 was $4.45 million, 15% higher than just three years ago.
With such high stakes, investing in a robust email authentication solution just makes good financial sense.
How to set up DMARC
Since DMARC is a must-have for your email marketing, here’s a step-by-step guide to setting it up.
1. Identify your email sources
Start by identifying all the legitimate sources emails get sent from using your domain name.
Then you’ll need to make a list of email servers used internally in your company, marketing services like Mailchimp, and any other services that send emails on your behalf.
2. Configure SPF and DKIM
Next, publish the list of approved email sources in your domain’s SPF settings. Below, you can see the SPF settings for a domain and what each setting means:
For DKIM, you’ll need to create two encryption keys — public and private.
The public key should be published in your domain’s settings. The approved email sources you listed will use the private key to digitally “sign” all outgoing emails from your domain to prove they’re authentic.
Here is what the DomainKeys setup interface might look like:
If SPF and DKIM aren’t set up correctly, your domain could be blacklisted and emails could land in spam.
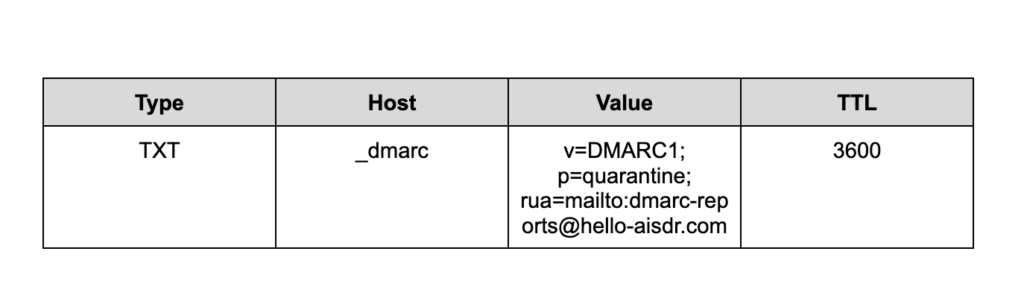
3. Create a DMARC record
Your DMARC record is a text file that states what you want to happen to emails that fail authentication. There are three options, which you specify using the “p” tag in the text string.
- p=none: just monitor (report) failed emails
- p=quarantine: send failed emails to the spam folder
- p=reject: block these emails (do not deliver)
The table below is an example using the domain “hello-aisdr.com”.
You can copy the values directly since they are universal, but don’t forget to change the domain in “Value” to your domain.
4. Publish the DMARC record in the DNS
After creating your DMARC record, you can publish it to your domain’s DNS. Email providers will then check the DMARC settings and follow the instructions for dealing with any emails trying to use your domain.
5. Adjust your DMARC policy as necessary
Some companies start by setting up DMARC just to monitor emails.
This mode doesn’t actually block email delivery. Instead, you get reports about any emails that failed authentication so you can investigate where they came from. Then you can update your email security practices based on the report results.
Here are the steps on how to start the monitoring mode. Specifically, the p=none policy indicates that no action will be taken should an email fail authentication.
Why set up DMARC?
DMARC lets you fight back against email spammers. As a result, you:
- Improve your email deliverability. Email providers look more favorably on domains implementing DMARC, meaning your legitimate messages get delivered properly.
- Increase brand trust. By blocking spoofed emails with DMARC, you can ensure that your customers and prospects never see a fake or malicious email claiming to be from your company.
- Save money. A proper DMARC setup will help you protect your company from non-compliance fines.











